Your engineers are already using coding agents.
Next up is product, finance, and sales – the whole company.
How do you get your arms around agent adoption?
Scope
Get the permissions house in order
Every user in your org has permissions. Most have too many.
Oso maps this posture: who has access to what, classified by risk. Then it recommends what to scope down — before agents inherit the mess.

Watch
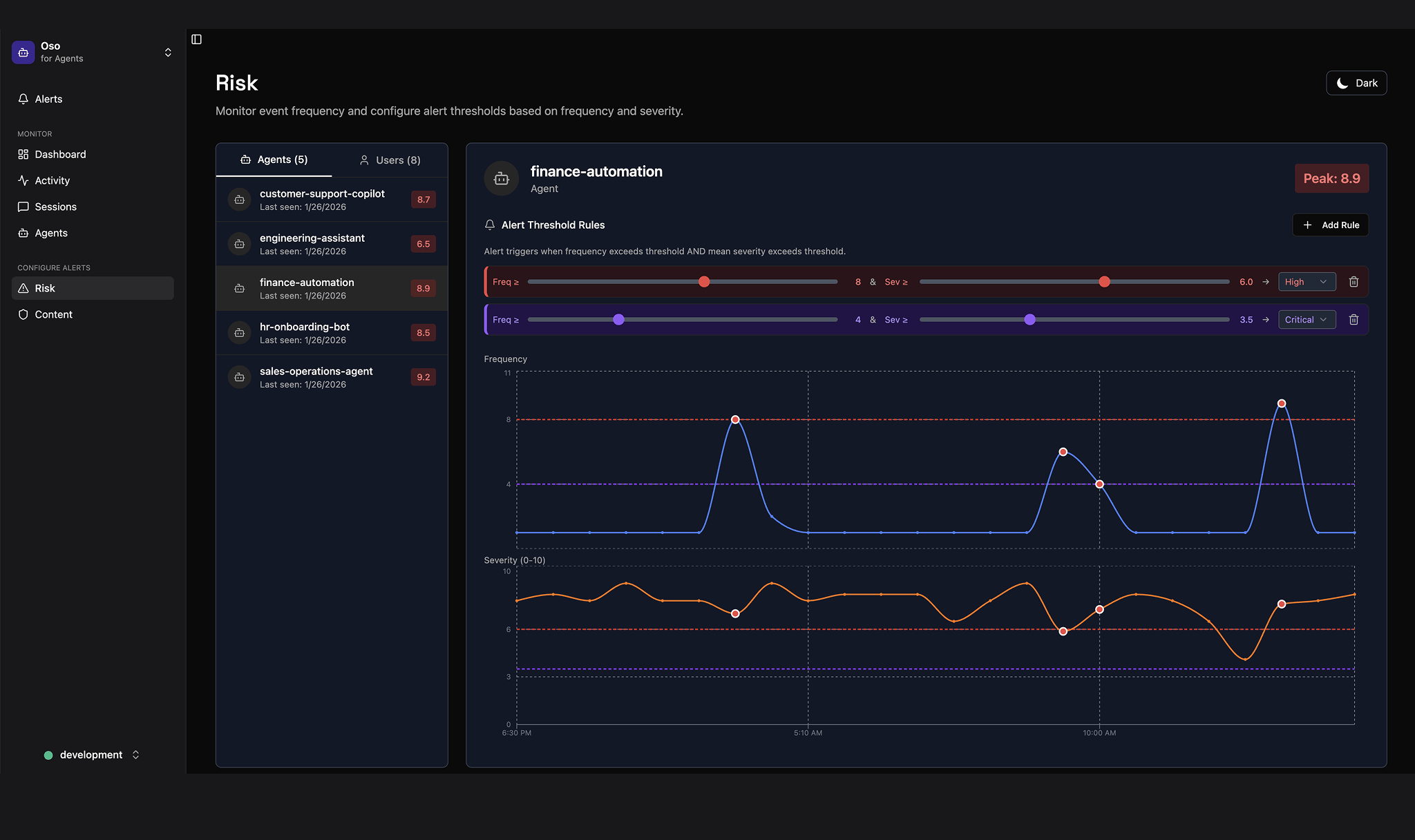
See what agents are doing
Every prompt, every tool call, every MCP server — captured in real time.
Default alerts for PII exfiltration, unusual velocity, and access to sensitive resources. Add your own rules in minutes.
When agents exceed least privilege, you know immediately.

Enforce
Narrow access automatically as risk builds
Permission risk isn’t static. It’s a function of the user, the agent, and the session so far.
As risk climbs, access narrows — automatically.
High-risk actions go through deterministic controls. Block agents from leaking data, modifying critical infra, or breaking any rule you set.
Audit
Keep receipts
Full trails of every action, tool call, command, and LLM response.
Backwards visibility to handle incident response and post-mortems.
Reports on agent posture and proof that you're on top of it.
Compliance records for auditors.




























